Cross-site scripting attacks (XSS), are a type of attack in which malicious scripts are injected into websites and web applications and run on an end user’s platform. Vulnerable endpoints are found and JS code is injected to execute it for malicious purposes. Such endpoints can be search fields, profile information fields, file upload functions and many more.
An authenticated attack refers to the conditions where an attacker must be logged to exploit the vulnerability. In OpenCart 3.0.3.2 it is possible to execute cross site scripting attack since the profile image upload feature in admin panel is not escaping user inputs.
To execute follow the steps below.
- Login to the admin panel, navigate to system > users > edit an existing user.
- Go to the Image change section and select a file with the XSS payload as
"><svg onload=alert("XSS")>and save it. - Thats it.

What’s the solution ???
The Same payload gets executed for the directory name too. So, I suggested a regex which replaces special characters in filename/directory names with whitespaces and removes white spaces too.
// Sanitize the filename
$filename = basename(html_entity_decode($file['name'], ENT_QUOTES, 'UTF-8'));
//Using regex to filter filename
$filename=preg_replace('/[^A-Za-z0-9\-\.]/','',$filename);
// Validate the filename length
if ((utf8_strlen($filename) < 3) || (utf8_strlen($filename) > 255)) {
$json['error'] = $this->language->get('error_filename');
}
class GO_Example_Model_Thing extends GO_Base_Db_ActiveRecord {
...
Outcome:
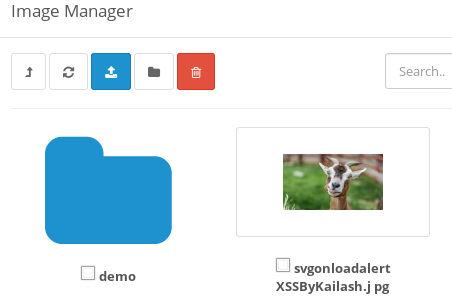
But this won’t work if the file containing the payload is uploaded using the FTP service. So one of the solution on issue I have opened on GitHub was preg_replace('/[^a-zA-Z0-9\_\.\?]/', '', basename(html_entity_decode($this->request->post['x'], ENT_QUOTES, 'UTF-8'))); by straightlight. Let’s see how they add a fix in the main code of the opencart in the next release.