Two different cross site scripting vulnerabilities were found on version below 20.0.1 and reported to Mdaemon team. As per the resposne from their side both issues were addressed on latest version 20.0.1 released on 18th August 2020.
Case One:
E-mail attachment field is vulnerable to XSS. A attachment with XSS payload as a file name can be uploaded to trigger execution of code. To do that follow steps below:
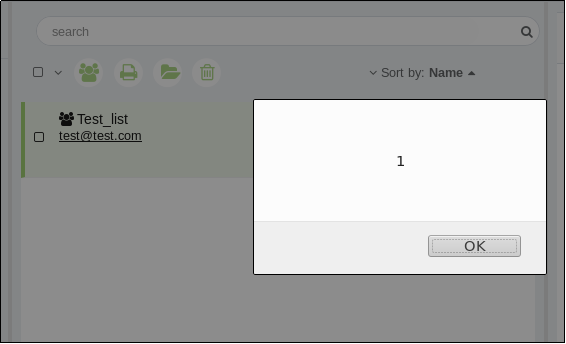
- Rename a file and set it’s name as
<img src=x onerror=alert(1)>.jpg - Go to New mail, select recipient and the select attachment. Code gets executed as right after upload so it becomes self XSS.
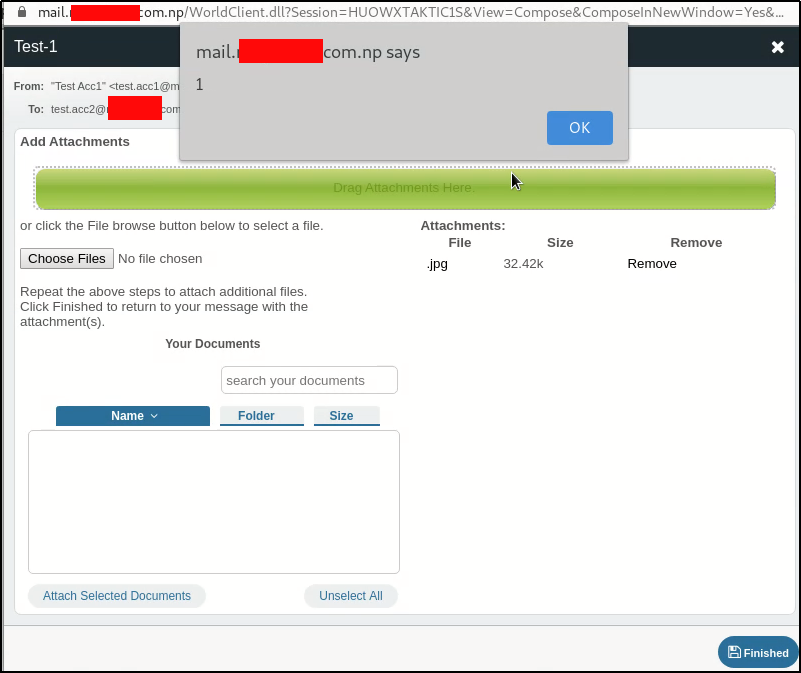
- Let’s send the mail to recipient and open from his/her side. Opening just a mail doesn’t executes the code but when the victim clicks on forward button, XSS pop-up is shown.
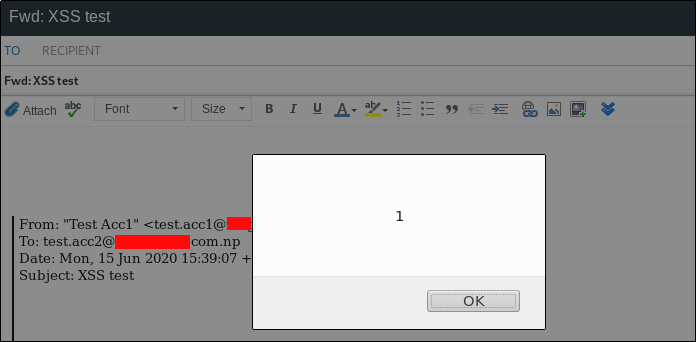 Like this a stored self XSS can also becomes perfect XSS for victim users.
Like this a stored self XSS can also becomes perfect XSS for victim users.
Case Two:
So the next vulnerable endpoint is Distribution list. A distribution list holds name and email address of persons. We can also refer it as a address book. Following steps can be followed to execute the vulnerability.
- Go to contact section and distribution list menu. Create a new distribution list.
- Contact name field was vulnerable to XSS. Use the payload
<img src=x onerror=alert(1)>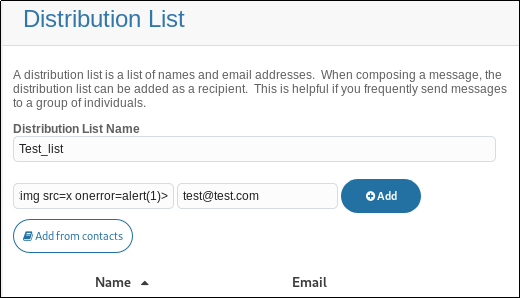
- We can see execution code and after saving it, each time we visits the distribution list section the XSS pop-up is seen.